Features
Full threat visualization
Monitor network and handset
activity.
Multiple-platform support
Monitors security events
across a broad range of mobile
operating systems and network
hardware.
Correlated reporting
Real-time, correlated
monitoring and reporting
across the network and
handset, providing a holistic
view into the security posture
of the network.
Performance optimization
Our optimized design
guarantees accelerated
processing, while minimizing
the amount of server hardware
required.
Industrial strength scalability
Supports multi-gigabit
bandwidth rates.
Distributed architecture
Allows for easy integration into
any network topology.
Always on, always
accessible
Web reporting engine supports
local and remote access.
Multiple-traffic bearers
Monitors across all traffic
bearers, including WAP and
web traffic, SMS/MMS, BREW,
and 3G data services.
Real-time Alerts
SMS/Email alarms and
notifications.
Forensic Search
Built-in search mechanism
enables user-defined queries
for historical attack
investigation and analysis.
Log file auto-archiving
Store log files in compressed
format for future investigation.
ODBC Support
Supports integration with
existing database and
reporting systems for
centralized reporting.
|
System Requirements |
• Processor – Pentium 4 –
2.4 GHz or higher
• Disk Space – 20 GB or higher
• RAM - 2GB or higher
• Operating System –
Windows Server 2003 /
Linux 2.6+ / *NIX
• Browser -Internet Explorer
6.0, Mozilla Firefox
• Database - PostGres 8.0+ /
Oracle 8i+ / MSSQL 2003+ /
Web Sphere
• WebServer - Apache 2.0+ /
IIS / ASP.NET 2.0
• Application Servers - Web
Sphere / Jboss
• Mobile Platforms - Symbian,
Windows Mobile,
RIM Blackberry, Palm,
Linux, J2ME, BREW |
|
Each security component within the SMobile Core Anti-Abuse
Engine can be customized, allowing the operator to implement only the security solutions
required for their customer base. Furthermore, additional components can be added as
they are required in the future. For example, an initial deployment may include only anti-
virus and anti-spam, with content and image filtering added in a later phase.
Security architectures typically require three layers of functionality. A policy decision layer
that provides the service control decision logic, a policy enforcement layer that executes on
the decision passed to it by the policy decision layer, and a backend database layer where
the policies, virus signatures, URL categories, etc are stored.
SMobile’s Core Anti-Abuse Engine provides the functionality required for the policy
enforcement layer to support value added security services like anti-virus, anti-spam,
content filtering and intrusion prevention. It provides deep packet inspection for multiple
protocols and data traffic bearers, and following packet inspection the Core Anti-Abuse
engine supports further protocol analysis. With appropriate interfaces it can then provide
policy enforcement based on the policies, rules, services plans and decisions made by the
policy decision layer.
Easy Deployment 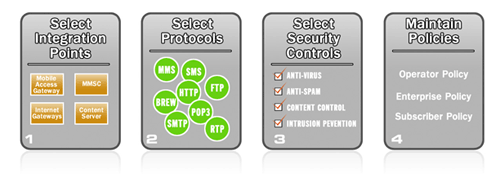
|
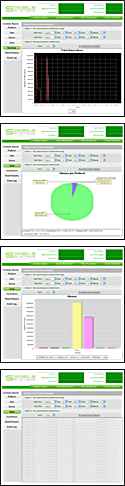
While log files contain a wealth of data, turning large amounts of log data into
understandable, actionable information can be challenging and time consuming. This is not
the case with CoreStats™, where data is collected and consolidated into concise, pre-
defined and custom-built reports that make sense and provide added value to your security
investment decisions.
CoreStats™ reports are organized into five intuitive categories: security, users, content
control, network, and handsets. Carriers with more detailed requirements can use
customizable filters to modify existing reports, or to create their own unique versions.
CoreStats™ also enables archival or deletion of records based on needs of administrators.
This allows for easy, automated database maintenance.
Carriers rely on business intelligence systems to track and manage day-to-day operations,
and to better serve their customers. CoreStats™ integrates into existing business
intelligence systems, providing valuable, previously unavailable information to help you
better serve your customers. CoreStats™ works with business intelligence software from
global leaders such as Business Objects, Hyperion Solutions, Cognos and others.
With CoreStats™ you will add unique, never before captured information and value-added services, allowing the administrator to reap the benefits of the only fully integrated industrial strength mobile intelligence system on the market today.
The following are some example reports that are supported by tabular and graphical representation:
Security Reports
• Most prolific viruses
• Average infections per day
• “Threat Level” of attack
• Regional reporting, virus traffic data based on regions
User Reports
• Number of infected requests (% of total)
• Detailed subscriber information
• Continuous monitoring of suspicious users (defined length of time)
• Number of times a particular subscriber has been infected
Content Control Reports
• List of blocked URL requests
• Number of Spam messages
• List of blocked content and questionable applications
(ie. Spyware, IM, VOIP, and P2P)
• Detailed restricted image analysis
Network Reports
• Percentage of traffic that is virus based
• % of bandwidth consumed over air interface
• Anomaly and DoS threat analysis
• Aggregate Infection Trends
Handset reports
• Top platforms affected
• # of infections per platform
CoreStats™ provides operators the ability to customize reports on any information collected. The reports are time scalable to a day, week, month, quarter or year.
Additional Features
• SMS subscriber with notification of infection
• Data Export (CVS and other formats)
• Internal alarms and notifications |
 |
<<back
|
|